ServiceNow
Alert Logic Integration with ServiceNow allows you to:
- Generate a ServiceNow Incident when Alert Logic detects a Security Incident or Security Observation.
- Generate a ServiceNow Incident in response to a scheduled search or report execution.
Supported subscription types
- Managed Detection and Response Essentials
- Managed Detection and Response Professional
- Alert Logic Cloud Defender
The types of notifications you can send to ServiceNow depend on your subscription type.
Architecture diagram
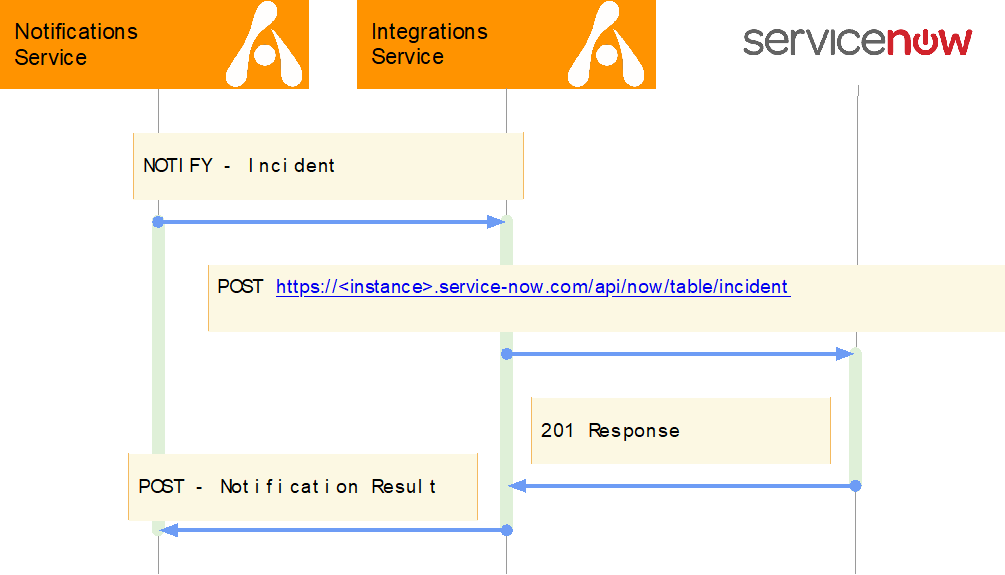
Click image to expand
Overview
- When Alert Logic generates an incident, observation, report, or other record, the Alert Logic Notification Service is notified.
- When there are active subscriptions that match notification criteria and use Integration as a notification target, the Integrations Service is called to deliver a notification to a target integration.
- The Integration Service applies any JSON transformations configured for a target Integration connection (in this example, ServiceNow).
- Integration Service executes HTTP POST request against target integration.
- Response status of HTTP POST is recorded and is accessible via audit trails.
Deployment and Configuration
For information on how to configure connections with ServiceNow, see Configure ServiceNow Connection and Configure ServiceNow Templated Connection .
Best Practices
For incident notifications, Alert Logic recommends you toggle Escalations on and only create tickets for high and critical incidents to start with. You can always add lower severity incidents later. If you do not toggle escalations on, you will receive incidents when they are created automatically and not after the SOC team analyzes it.